Understanding 2FA: Comparing SMS, Authenticator Apps, and Hardware Keys
08 September 2025
4 min for read
Why 2FA Still Matters—and Why Choosing the Right Method Is Crucial
Two-factor authentication (2FA) remains one of the most effective ways to protect online accounts. Yet not all 2FA methods offer the same level of protection. SMS-based verification is widely used due to convenience, but comes with serious vulnerabilities. Authenticator apps are generally more secure, but they’re not without risks. And at the top of the security spectrum are hardware security keys—currently the most reliable option available.
In this article, we’ll break down how different 2FA methods work, their respective strengths and weaknesses, and which one is best for your specific needs.

How SMS 2FA Works and Where It Falls Short
SMS-based two-factor authentication operates by sending a one-time code to your phone number after you've entered your password. You then input this code to verify your identity.
While simple and accessible, SMS was never designed with security in mind. Messages are sent over unencrypted channels, making them vulnerable to interception. Worse still, SMS 2FA is prone to SIM-swapping attacks. This type of attack involves convincing your mobile provider to transfer your number to a SIM they control, effectively hijacking your messages and calls.
Real-world examples highlight the danger: In 2018, a SIM-swapping attack led to the theft of $24 million from a crypto investor. In 2019, Twitter’s then-CEO Jack Dorsey had his account compromised through a similar attack.
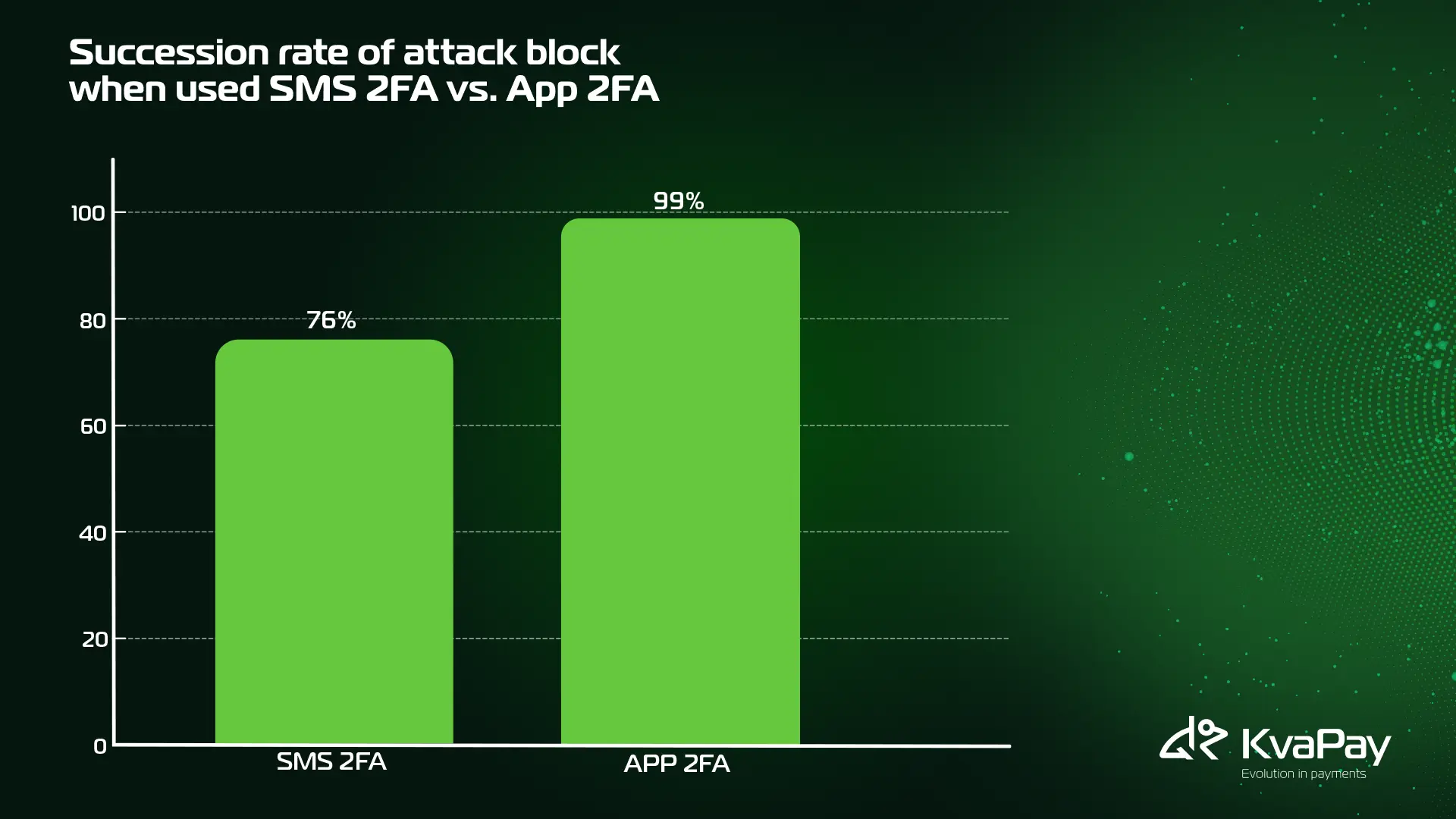
Despite these risks, SMS 2FA can still stop a majority of automated attacks—about 76%, according to Forrester. But that leaves nearly a quarter of threats unaddressed.
It's worth noting that at KvaPay, SMS verification is used only for basic identity checks. Not for signing or sensitive transactions, which rely on stronger methods.
How Authenticator Apps Work and What to Watch Out For
Authenticator apps generate time-based one-time passwords (TOTPs) using a shared secret key and your device’s clock. Once paired with an account (typically by scanning a QR code), the app generates rotating codes every 30 seconds that don’t require a network connection to work.
This method addresses many of SMS’s weaknesses:
- No transmission risk: Codes are generated locally.
- No SIM dependency: Your phone number doesn’t factor in.
- Short lifespan: Codes expire quickly, reducing attack windows.
- Offline functionality: Codes work without mobile service or Wi-Fi.
However, TOTP is not immune to compromise. If an attacker gains access to the original QR code (during setup), the shared secret used to generate codes, or directly compromises your device, they can generate valid 2FA codes themselves—completely bypassing the app's protection. This is especially dangerous in cases where users back up QR codes insecurely or store screenshots in cloud services.
Additionally, server-side vulnerabilities like cross-site scripting (XSS), SQL injection, or poorly secured APIs can lead to attackers extracting secret keys or session tokens. These backend threats are often overlooked but can render even TOTP-based protections ineffective.
Despite these caveats, authenticator apps still offer better protection than SMS in most scenarios. In a study by Microsoft, on-device authenticators blocked:
- 100% of automated bots
- 99% of bulk phishing attacks
- 90% of targeted attacks

The Gold Standard: Hardware Security Keys
While authenticator apps are a major step up from SMS, hardware security keys offer even stronger protection. These physical devices (like YubiKeys) plug into your computer or connect via NFC, and cannot be intercepted, cloned, or phished.
Unlike TOTP, which is susceptible to shared secret leaks, hardware keys use public-key cryptography and don’t expose any sensitive data. Even if the device is stolen. They also often require a physical tap or touch, adding another layer of intent-based authentication.

Their main downsides? They cost money, can be misplaced, and aren’t supported by all platforms yet. But for critical accounts, especially financial, cloud, and administrative tools, hardware keys are the best defense available.
Which 2FA Method Should You Use?
Here’s a quick breakdown of pros and cons:
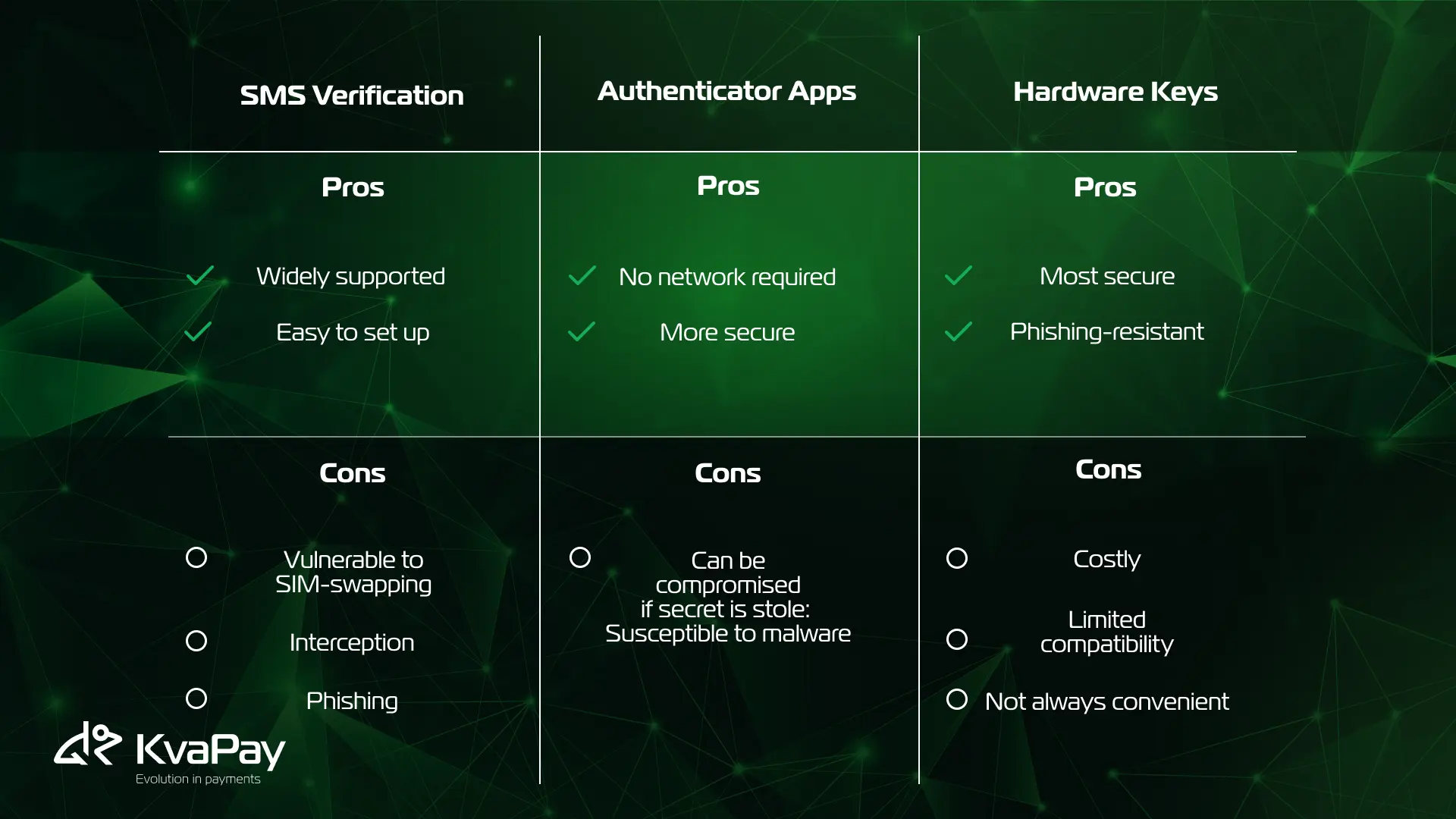
For most users, the best solution is a combination of authenticator apps and hardware keys. Use authenticator apps for everyday accounts, and reserve hardware keys for critical logins. Avoid SMS 2FA wherever possible, or use it only as a fallback.
Security is never absolute, but your defenses should evolve with the threats. While SMS-based 2FA still offers basic protection, it’s increasingly outmatched by modern attack techniques. Authenticator apps provide a strong middle ground—if implemented carefully. And for those seeking maximum security, hardware keys remain the gold standard.
At KvaPay, we strongly encourage users to enable 2FA and consider hardware-based options for sensitive transactions. Your digital identity is only as safe as the methods you use to protect it.

